FTP Data Exfiltration Investigation
- BlueDolphin
- Apr 4, 2025
- 3 min read
YouTube Video
Scenario
A major incident has recently occurred at Forela. Approximately 20 GB of data were stolen from internal s3 buckets and the attackers are now extorting Forela. During the root cause analysis, an FTP server was suspected to be the source of the attack. It was found that this server was also compromised and some data was stolen, leading to further compromises throughout the environment. You are provided with a minimal PCAP file. Your goal is to find evidence of brute force and data exfiltration.
Noteable Observations
Bruteforce attack
Data Exfiltration via RETR S3 Bucket commands
Tools used:
Wireshark
IP Address lookup
References:
Try the lab for yourself over at: https://app.hackthebox.com/sherlocks/Origins
Wireshark exporting data: https://www.wireshark.org/docs/wsug_html_chunked/ChIOExportSection.html
FTP-RETR Command https://www.solarwinds.com/serv-u/tutorials/appe-stor-stou-retr-list-mlsd-mlst-ftp-command

What is the attacker's IP address?
In the wireshark capture, we can see a bruteforce pattern, which suggests this could be the attacker, and sure enough the IP address is accepted.
15.206.185.207

It's critical to get more knowledge about the attackers, even if it's low fidelity. Using the geolocation data of the IP address used by the attackers, what city do they belong to?
Taking the above IP address and passing this into an IP address lookup tools reveals the IP belongs to Mumbai.

Which FTP application was used by the backup server? Enter the full name and version. (Format: Name Version)
vsFTPD 3.0.5 is disclosed in the information tab of the servers FTP response.

The attacker has started a brute force attack on the server. When did this attack start?
This was an easy one, looking for the first login request to the FTP server will reveal the answer. Keep in mind the UTC time is required for this answer.
2024-05-03 04:12:54

What are the correct credentials that gave the attacker access? (Format username:password)
Finding the login successful server response will get you started on the right track. However given that there were multiple network streams happening concurrently, you can simply go back a few packets with easy.
Reviewing the Stream index which in this case is number 5, and following that stream will reveal the authentication and thus the utilized credentials.


The attacker has exfiltrated files from the server. What is the FTP command used to download the remote files?
For this challenge, the sweet spot is to locate and investigate right before the "Transer complete" server response.

Afterthoughts:
The RETR s3_bucket command in a packet suggests an FTP command where RETR (short for "Retrieve") is used to download a file from an FTP server. However, in the context of Amazon S3, this is unusual because S3 does not use traditional FTP commands. Instead, S3 typically relies on REST API calls, the AWS CLI, or SDKs.
Some malware or attackers use FTP-like commands over non-standard protocols to exfiltrate data.
Some cloud services allow users to interact with storage using an FTP-like interface, translating RETR to an S3 API GET request.
Attackers were able to compromise the credentials of a backup SSH server. What is the password for this SSH server?
At this stage, we assume the attacker is now inside the server via the previous bruteforce attack that led to a successful login. Looking for horizontal movement would lead you to check what files had been downloaded. This can be performed by using the wireshark export object option.

The Maintenance-Notice PDF reads:
For team members requiring urgent access to the backup SSH servers during the maintenance
period, you can use the temporary password "**B@ckup2024!**" - kindly ensure this information is handled securely and do not share it outside of our team.
What is the s3 bucket URL for the data archive from 2023?
For this challenge, if we re-visit the packets performing data exfiltration with our previously identified command, we will see the name of the URL in the "text data" portion of the request.
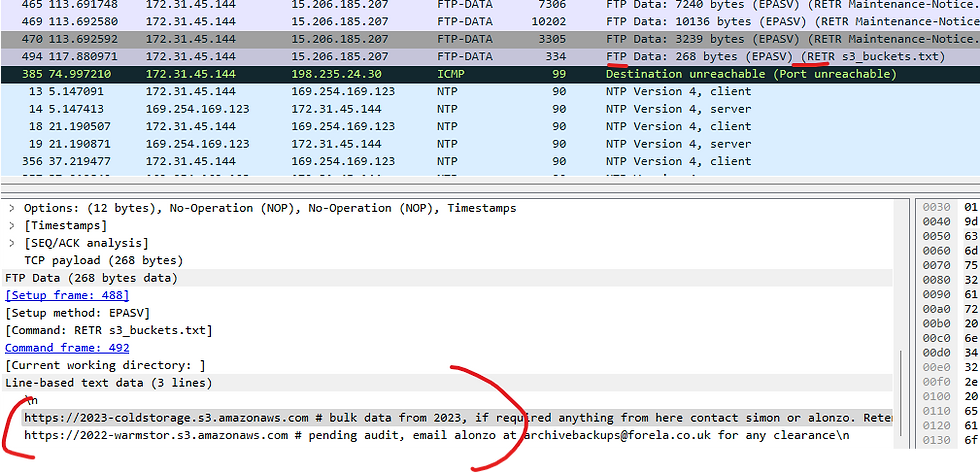
The scope of the incident is huge as Forela's s3 buckets were also compromised and several GB of data were stolen and leaked. It was also discovered that the attackers used social engineering to gain access to sensitive data and extort it. What is the internal email address used by the attacker in the phishing email to gain access to sensitive data stored on s3 buckets?
For this challenge, the idea is the attacker continued to establish a foothold by changing the contact banner for the S3bucket to a compromised email, with the context of requesting clearance.





Comments