Hack the Box - WEB - Juggling facts
- BlueDolphin
- Feb 3, 2024
- 1 min read
Updated: Mar 3, 2024
CHALLENGE DESCRIPTION
An organization seems to possess knowledge of the true nature of pumpkins. Can you find out what they honestly know and uncover this centuries-long secret once and for all?
Solution Summary
Enumerate web application
Source code review
Exploitation
References
1) Enumerate web application
We start by reviewing the web application. It appears as a basic web application with only 3 user facing objects that appear to be interactive.
Clicking on the 'Secret Facts" link brings us to an interesting page where it appears that there are resources "Secrets" which can only be access by an administrator.
2) Source Code Review
Source Code Review Summary
Our target application is has a secrets section on the webpage that we don't have permissions to access. Analyzing the source code reveals that the php application is looking for data type "secrets", and not a remote address in order to reveal the flag.
If I understand correctly, PHP Type Juggling is the attack surface, but there is no loose comparison, so we want to pop the first switch case "secrets" by passing data type "true"
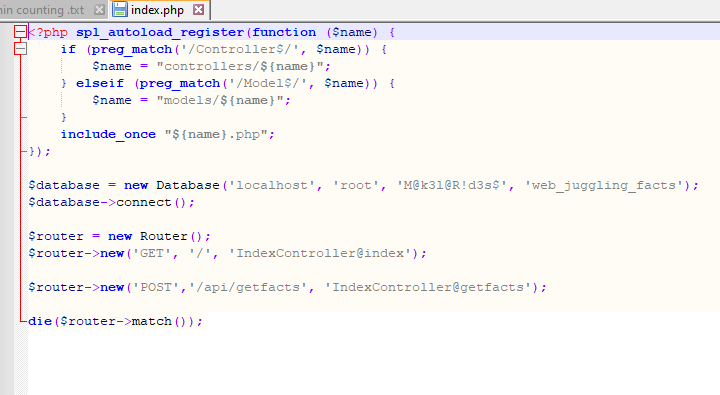
I found source code review to be time consuming and can often send me in multiple directions. For this challenged I started high level with the index file seen below. The index file contains interesting variables, functions, credentials, and workflow data.
Firstly, the user root and the corresponding password. This is probably so we can setup the lab locally for testing via the docker file that was provided with the challenge.
Secondly is the controller and model directory found in the function spl_autoload_register.
Thirdly is the variables $database and $router. When conjoined with the api workflow that we can identify in the $router variable, we should be narrowing down our attack surface.
Eventually you will make your way across the "Index Controller(.)php file which will provide us our next step in this challenge. I can break down the below code into 4 important points.
The function is looking for data, I suspect this is user input. public function getfacts($router)
The if statement is checking if the user input is type secrets AND the remote address is a local host. The local host part I think is geared towards the provided files which allow us to spin up a local service via Docker. Here we do not have a vulnerability as the strict type comparison was used "===". if ($jsondata['type'] === 'secrets' && $_SERVER['REMOTE_ADDR'] !== '127.0.0.1')
A switch case is defined based on user input. However, there is no vulnerability as "===" and "!==" are strict comparisons. switch ($jsondata['type'])
This is where the magic happens. We actually don't have vulnerable code in the traditional sense as it relates to PHP. What we instead have is a switch case misconfiguration. While I didn't realize this until I had finished solving the challenge and asked around for help as I was confused why my solution worked.
Having found that there is a route to 'secrets' but we don't know what it is. Further exploring into the "entrypoint.sh" file which is a file that runs with the docker container at start reveals it holds the flag.
3) Exploitation
Browsing to our target web page reveals this landing page. The "secret facts" button in the top right is hiding our flag.
Browsing to "Secret Facts" provides us with a page and a message making it clear that only the administrators can access secrets. On the left side, we can see the burp request in which the Data Type is a string and that string is a secret. Attempting to pass the spooky and not spooky switch cases just moved me around the website and did not bring me closer to the secrets.
This is a strict comparison table to determine Boolean evaluations. It didn't really help me a whole lot other than realizing that perhaps the data type can be true and it will execute the use cases.
Sure enough changing the type to true evaluated as true and popped the first switch case. So if the secrets
We can see here that we didn't actually exploit a comparison variable, but passed the data type as true and the backend accepted this and revealed the first case which is 'secrets'. If secrets had been further down, this would not of worked.













Comments