Process Injection Investigation (TLS Callback)
- BlueDolphin
- Dec 4, 2025
- 3 min read

Scenario:
Byte Doctor suspects the attacker used a process injection technique to run malicious code within a legitimate process, leaving minimal traces on the file system. The logs reveal Win32 API calls that hint at a specific injection method used in the attack. Your task is to analyze these logs using a tool called API Monitor to uncover the injection technique and identify which legitimate process was targeted.
Index:
Overview
Our approach
Malicious binary review
Windows API activity log review
Overview:
Tools Used:
IDA disassembler
API Monitor V2
References:
Assembly Architecture Reference:
RDI register - is a destination index that holds the first argument passed to a function or sys call.
RAX register - is the accumulator register and used for arithmetic operations, before returning the result to the main function.
Techniques Observed:
Process Injection
TLS callback abuse
Obfuscation race condition
Evidence provided:
.apmx64 file - This is a log file of API calls made by an application or service.
inject.exe - Malicious file used by the attacker
Our approach:
We are going to first investigate the malicious binary to learn more about our payload. We are then going to view the API log file to learn what transpired on the host when the malicious binary was loaded. This will require us to identify the process injection technique, and step through the API calls/actions made by inject.exe on the system.
We are going to uncover the following:
What process injection technique was used
Which Win32 API was used to enumerate processes and threads on the system
Which process the attacker is targeting for payload injection
The size of the payload
Which Win32 API actually executed the injected payload
Malicious binary review:
Opening up the file in IDA the first major piece of evidence is found under the export tab. This shows us which functions in our binary, have been made available for other applications or services. This is a key component in process injection, as the the malicious function needs to be available for a remote call.
We see the TlsCallback before the Main function, which appears likes obfuscation which results in the malicious program running before the legitimate programs main entry point is reached. It is safe to say the process injection technique is specific to "TlsCallBack"

inject.exe - export tab
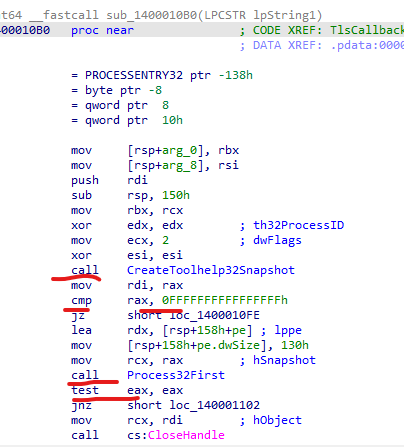
Next, we review the programs application logic and notice very quickly that the process injection is the first thing to execute in this programs workflow. It clearly shows the TlsCallback process being initiated and then proceeds to enumerate the local system for a process and once the process is found, a cmp operator is run, likely to compare the list of found processes with a specific one the malware is looking for.
The process injection sub routine logic can be seen below.

Moving further down the applications logic and work flow, we see that the program also calls CreateToolhelp32Snapshot which is used to observe what processes are running on a host at the given time. We then see the value from RDI is moved into RAX and compared against something stored in memory, at a very early address which makes me think it is a defined global variable representing the process that the attacker is on the hunt for.
RDI register - is a destination index that holds the first argument passed to a function or sys call.
RAX register - is the accumulator register and used for arithmetic operations, before returning the result to the main function.
Windows API activity log review
We can see that the malicious binary has a module called inject.exe, and the first few lines reveal that this module is making API calls with "CreateToolHelp32Snapshopt" which is used to enumerate running processes on a system. From there, it starts to perform a iterative loop whereby it checks each process until it finds notepad.exe.

When indect.exe finally finds notepad.exe as a running process, it starts the injection attack which is characterized by the below actions;
Opens notepad.exe
Allocates memory in the target process address space
Writes data (shellcode)
Creates a remote thread to declare a new starting address. Function then returns a handle to the new thread.
Wait for remote threat to terminate
Cleanup.

That is in short what TLS callback process injection looks like, and how it can be identified in the real world. A big thanks to Hack the Box for creating a wonderful and informative lab.
END




Comments