Tampering Vulnerability Lab - Node JS
- BlueDolphin
- Jul 30, 2025
- 4 min read
Updated: Aug 15, 2025
Index
Intro
What is Parameter Tampering
Example of Insecure Code
Mitigation Strategies
Lab walkthrough
1) Intro
In modern web applications, data flows constantly between clients and servers. While this enables dynamic functionality, it also opens the door to attacks if user input is not properly validated. One common and dangerous threat is parameter tampering—where attackers modify request data to gain unauthorized access, escalate privileges, or manipulate transactions. In this post, we’ll explore how parameter tampering works in Node.js applications and how you can protect your app from these vulnerabilities.
2) What is Parameter Tampering
Parameter tampering occurs when an attacker modifies data sent from the client to the server. This can happen in:
Form submissions
JSON payloads in API requests
Query parameters in URLs
Cookies or session data
Attackers exploit this to:
Change their user role or privileges
Access other users’ data
Manipulate prices or transactions
Real Request/Response Example
Original (Safe-looking) Request:
POST /update-profile HTTP/1.1
Host: example.com
Content-Type: application/json
{
"userId": "123",
"role": "user",
"email": "alice@example.com"
}
Tampered Request (Attacker Changes Role):
POST /update-profile HTTP/1.1
Host: example.com
Content-Type: application/json
{
"userId": "123",
"role": "admin", <-- Tampered
"email": "alice@example.com"
}
Server Response if Vulnerable:
{
"success": true,
"message": "Profile updated",
"role": "admin"
}
Key Takeaway: The attacker successfully escalates privileges by modifying the request.
3) Example of Insecure Code
The server has a parameter tampering vulnerability that allows users to control the user Id variable. This can be exploited to change the userId on purchase orders to that of the administrator. These malicious orders are then processed under the administrator account in the web application.
a. Function "OrderPaymentForm" The server calls function orderPaymentForm, which then calls mapOrderFields, passing the requesting users ID and req body parameters.
b. Function "MapOrderFields "takes the userID and req body data and then updates the server side userID for the session with the userID provided by the user.
Because the userID is not hard-coded, it can be controlled by the user consequentially creating a vulnerability.
Line by line breakdown
1) mapOrderFields(userId, data)
A method which takes userId and data (the req body from method orderPaymentForm)
2) const order = {};
creates an empty object named order
3) order['userId'] = userId;
Adds the users ID to the order object as key userId.
4) let any = 0;
Initializes a counter for keys in data
5) for (var key in data)
Iterates over all properties in object data.
6) any++;
Increments the counter every time a key is found in data.
7) order[key] = data[key];
Copies each key value from data and writes into the empty object order.
8) return order;
If there was data, it returns the fully built order object.
Mitigation Strategies
Before we dive in, let's talk about some high level mitigation strategies.
Never trust client input: Always validate and sanitize.
Use server-side session data instead of relying on client-supplied IDs.
Use allowlists for fields that can be updated.
Perform regular security audits and code reviews.
Use automated testing tools like OWASP ZAP to check for tampering.
How I secured the code for the secure coding lab challenge.
To fix this, create a list of safe keys to allow only relevant keys from the user request. Then, hard-code the userId and verify that only allowed keys are merged.
1) Create safe key list for keys in use
const allowedFields = []
2) Hard code userId to all orders.
userId: userId
3) Verify only allowed keys
for (let keys of allowedFields)
4) Confirm appropriate indentation.
Lab Walkthrough
1) Web app enumeration
Start by adding an item to the cart on a simple shopping page.
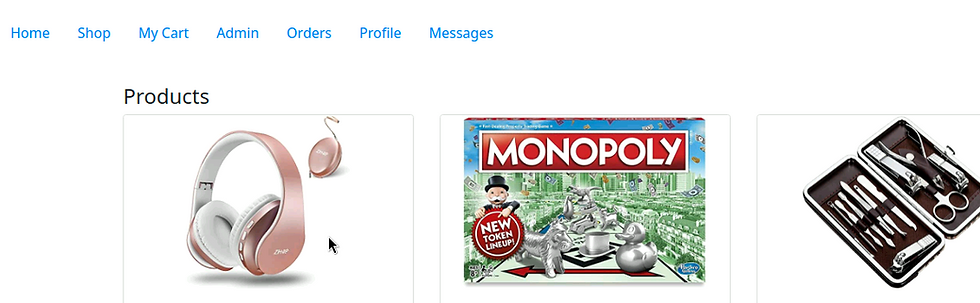
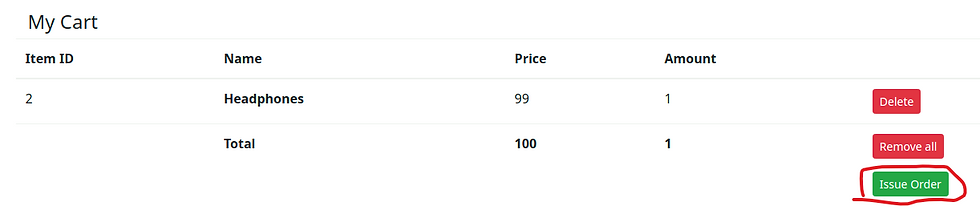
With an item in our shopping cart we will click the "Issue Order" button and observe the applications response.
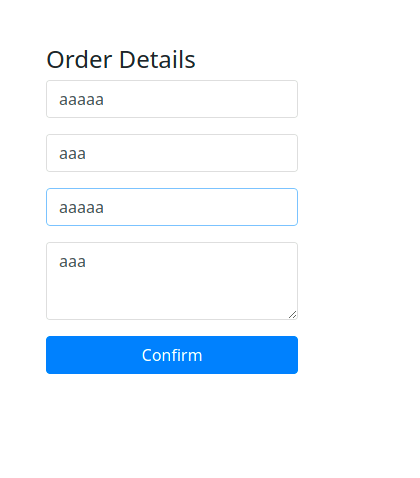
Filling out the order details form clicking "Confirm" submits the order.
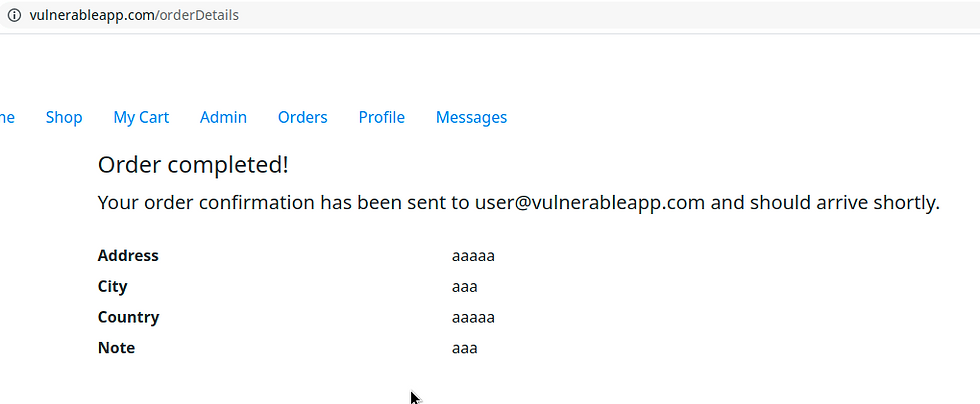
Here we are routed to the orderDetails endpoint where our order is completed. This is supposedly where the parameter tampering vulnerability resides.
2) Code review
Looking under "OrderController.js"
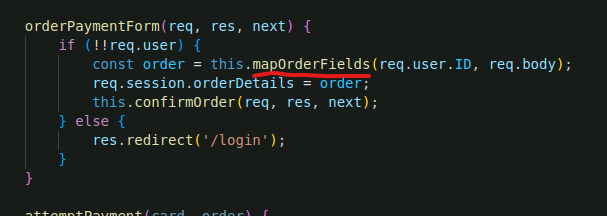
The code block below shows where the parameter tampering vulnerability is found. The web server accepts user controlled input mapped directly to the order object, which then appears on the orders page.
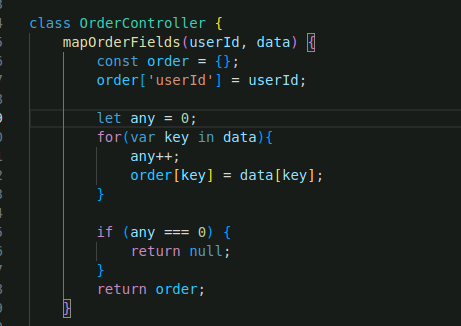
3) Recreate attack
Start by logging in, adding an item to the cart and then confirming that order. Intercept the request and add the userId field to the body of userId2 for the administrator. Sending this modified request will place the order as administrator and we can see the order logged under the administrators account.
Login
Add item to cart
Issue Order
Confirm order
Modify request to add userId: 2.
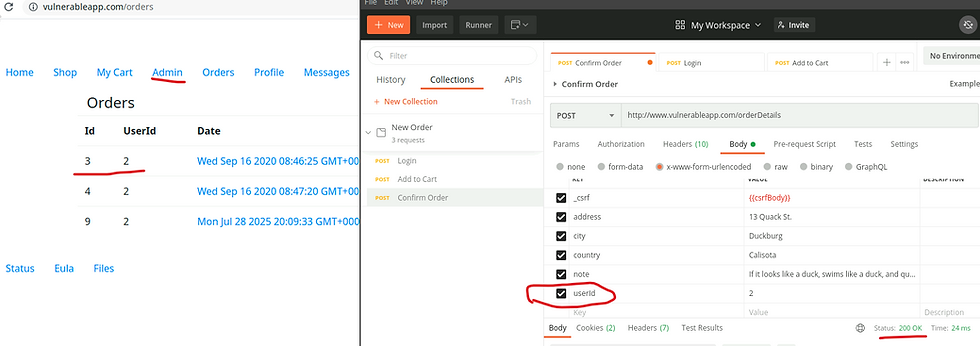
4) Revise code & patch server
Add a list of allowed fields to sanitize keys.
const allowedFields = []
Hard code userId to server
userId: userId
For loop to ensure the app continues only on allowed keys
for (let key of allowedFields)
Organization
Ensure good spacing, indentions and comments
5) Test and confirm patching
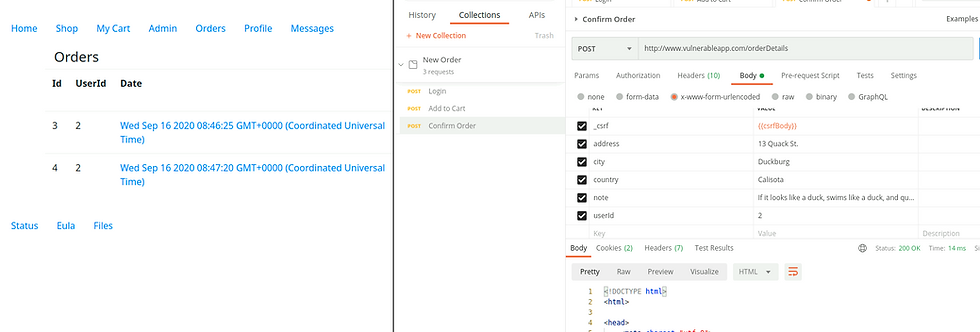
Here we place another order with the modified request. The malicious purchase did not appear under the administrators order history. This is great news and confirms the server is patched. So good!
THE END




Comments