Cascade - Hack The Box
- BlueDolphin
- Jul 31, 2020
- 4 min read
Cascade is an enumeration heavy Windows box. Initially we found account credentials in the custom LDAP attribute which allowed us to enumerate SMB shares uncovering VNC credentials which were then decrypted. With these credentials we were able to locate an SQlitedatabase that contained encryped credentials for the second user. In order to decrypt the credentials we had to reverse a .NET application. The privillege escalation stage involves extracting the admin password from the Active Directory tombstone, which is a feature for AD deleted objects.
Summary
Acquire list of users from the LDAP directory.
Find the password for user r.thompson in the cascadeLegacyPwd LDAP attribute.
Enumerate SMB shares data folder for VNC encrypted password for the user s.smith.
Decrypt VNC password and login.
Locate SQlite database and extract passwod for ArkSvc user.
Download .NET crypto appication, reverse engineer it and the find the cipher, key and IV to decrypt ArkSvc password.
Login is ArkSvc, acquire TempAdmin account from AD Tombstone and acquire flag.
Portscan

SMB Enumeration
We find that access is granted when connecting anonymously to the SMB shares. However there are no files listed which suggests we either do not have enough permissions or the SMB shares are just empty.

RPC Client
We attempt to login to the rpcclient as we know that the anonymous user login was allowed when tested against the smb shares. We manage to get a successful connection with an RPC shell.

Once connected in we can run a standard RPC command "enumdomusers" which retrieves and returns all active users who have used the client. This is a juicy target and gives us many user names and we prioritize arksvc at it is suggested to be a service related account which often is associated with elevated permissions. The other is BackupSvc which suggests backups are being performed and this service account is going to have read permissions. In a real environment it is quite common for administrators to provide domain admin privileges to service accounts in order to ensure the service accounts can perform without issues.

LDAP Enumeration
We run a basic ldap check requesting all available information with the ldapsearch tool. The results returned consist of all users in the domain and one of the users in particular, Ryan Thompson returns a LegactPwd attribute with a base64 encoded password.
ldapsearch -h 10.10.10.182 -p 389 -x -b "dc=cascade,dc=local"

The base64 text decodes into a string that we need to test as the password.

We can validate the credentials by attempting an authentication against the open SMB shares.

Great! The password worked and we are in with fill read permissions on the SMB folders. This is our initial foothold and we now look towards moving laterally and escalating to our next user.
Moving laterally
Unfortunately we were not able to login to the target host as user r.thompson with evil winrm, so we will try something different.
We connect to the SMB share as r.thompson and attempt to read the "Email Archives". However we are not able to output the contents of the file with "cat" or "type" so we download the file instead. This will allow us to grep and search the folder quickly.

Here we download the file with "mget".

After downloading the file we output the contents and see there is a suggestion of the TempAdmin account using the same password as the normal admin account. We do not know what this password is yet, but this is juicy information non the less.

VNC Log
While browsing around the shares we came across a file in the IT shared folder titled "VNC Logs". We downloaded this file with "mget" and displayed the content finding a password.

VNC passwords are encrypted with a custom DES cipher and key.
We download VNC decrypt from jeroennijhof's github, make and run the program.
Our output of the password is skewed, so a little

Upon downloading and running the application against our hex data, we receive a jumbled response.

We perform some research and learn the password is meant to be decrypted in binary format, and we convert to binary.
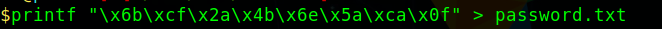
Running the program again, with our newly converted hex data yields the passwords.

User Flag
We connect in with Evil-winrm

We proceed to s.smith's desktop and cat the user flag.

Privilege escalation to root
After look around and running sherlock and winpeas I had not found anything concrete.
I revisited the file shares and realized I now had access to the audit share as s.smith.
SQLite3
In here I found a DB file and CascAudit.exe. After downloading these files, I first proceeded to work on the sql file.

I ran the file command on our audit.db file and we were shown that the file was apart of an SQLite 3 database.

I downloaded and installed SQLite and opened the Audit.db displaying all contents with the .tables and select * commands and found an encrypted password.

Unfortunately I could not crack this password, as when I decoded with base 64 it only gave me unreadable text.
Reversing Engineering
I proceeded to open the CascAudit.exe with visual studio to see if it was importing the CascCrypto.dll and sure enough it was. As I looked through the code, I found the encryption key, IV or initialization vector and the mode - CBC.


I went over to cyberchef and selected SQLite, inputted all relevant data and reeived the password for Arksvc.

Boom - I connected in as ArkSvc

Tombestone
From here I tried running enumeration scripts but did not find anything new as user ArkSvc, so I read over the forums and the hints suggested I go back to the email about temp admin and the deleted user. The only thing that made sense was to try and restore deleted users. Well I had not idea where to start without GUI, so I did some more looking around and realized that ArkSvc is a member of the AD Recycle Bin group.
I came across this article here about restoring deleted objects from AD.
I spent a while messing around, trying to get the switches to work and eventually had to narrow down my results to the specific user, and I finally got it with the following command.
Get-ADObject -Filter {displayName -eq "TempAdmin"} -IncludeDeletedObjects -Properties *

Base 64 decode gives us our password
YmFDVDNyMWFOMDBkbGVz = baCT3r1aN00dles





Comments